What Is Naoris Protocol?
Image: https://www.naorisprotocol.com/
In today’s digital age, Naoris Protocol is emerging as a significant protocol in cybersecurity. Naoris Protocol is a post-quantum-capable, self-validating cybersecurity protocol designed to build a decentralized Trust Mesh, restoring network trust between diverse devices and systems.
What is Naoris Protocol?
Naoris Protocol leverages post-quantum cryptography. It employs a custom dPoSec (Decentralized Proof of Security) consensus mechanism and a distributed SWARM AI framework to enable ongoing device-to-device validation and trust transfer. Unlike traditional centralized security systems, it operates as a distributed security network that becomes more robust as the community grows.
Core Technologies and Features
- Post-Quantum Cryptography: Uses encryption algorithms like Dilithium-5, compliant with NIST, NATO, and ETSI standards, to defend against security resistant to quantum computing threats.
- dPoSec Consensus: Devices act as nodes, directly validating and reaching consensus to form a self-validating security framework with no single point of failure, greatly enhancing network resilience.
- Distributed SWARM AI: Decentralized AI nodes work collaboratively to monitor, analyze, and respond to threats, enabling real-time defense and continuous learning.
Real-World Applications
- Enterprise and Government Security: Naoris Protocol allows organizations to share device security status in real time, facilitating cross-organizational compliance and trust.
- Web2 & Web3 Integrations: Traditional enterprise systems can incorporate Naoris for strengthened security. Blockchain nodes and smart contracts are scanned and validated in real time, ensuring quantum-resistant security.
$NAORIS Tokenomics Overview
1. Key Use Cases
$NAORIS is the core incentive mechanism driving validation and consensus across the protocol. Devices earn token rewards for performing validation tasks, sharing computing resources, and reporting security status, creating a community-powered contribute-and-earn token economy.
2. Incentive Mechanisms
- Device Validation Rewards: Devices that successfully participate in validations within the mesh network receive $NAORIS tokens.
- Node Staking: Running a full validator node requires locking a specific amount of $NAORIS tokens.
- Governance and Voting: Token holders are entitled to participate in node elections and protocol upgrade votes.
- Transaction verification and trust mechanism: All trust-based interactions and validations between devices are recorded and secured with tokens, functioning as verifiable proof of trusted operations.
3. Token Lock-Up and Release Model (Tokenomics)
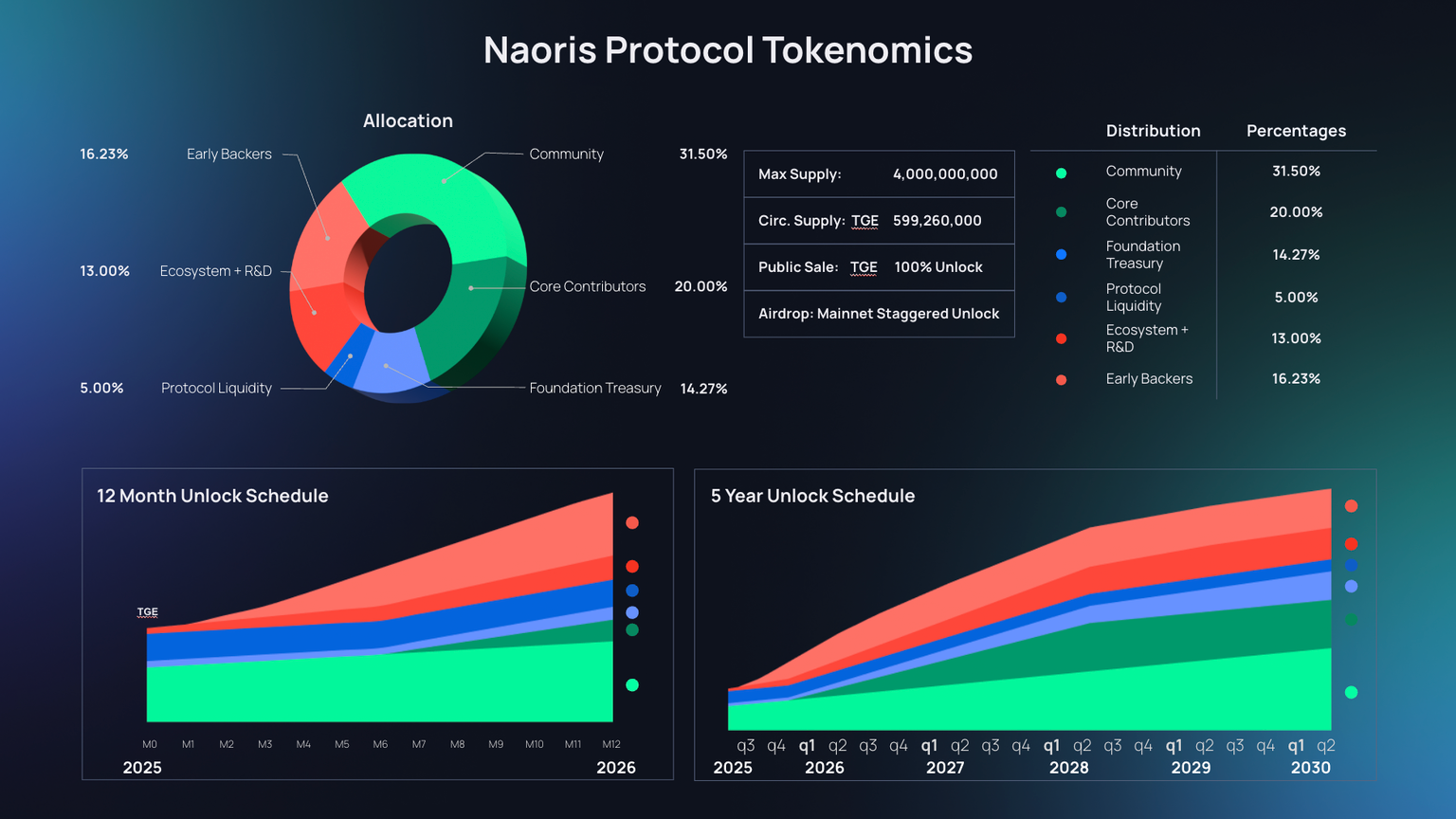
Image: https://knowledgebase.naorisprotocol.com/naoris-protocol/tokenomics/naoris-protocol-tokenomics
According to official documentation, Naoris Protocol has a total supply of 4 billion tokens, allocated as follows:
- Community Allocation (31.5%) is the largest, serving as a long-term incentive for ecosystem growth.
- Core Contributors (20%) and Early Supporters (16.23%) are unlocked over time to support long-term collaboration.
- The protocol distributes other allocations (foundation, R&D, liquidity) linearly over 12 months and 5 years, respectively.
4. Long-Term Value Potential
We expect usage frequency, validation utility, and secure transaction volume of $NAORIS to grow exponentially, powering strong value capture potential.
Why Choose Naoris Protocol?
- Quantum-resistant security for the future.
- Scalability and resilience from decentralization.
- Community-driven incentives: Devices validate and earn $NAORIS, creating a participatory trust ecosystem.
- Real-time proof of trust: Every operation, application, and connection is derived from a verifiable state of network security.
Naoris Protocol offers a community-centric approach to network trust and security.
Gate will be the first to launch Naoris Protocol (NAORIS) and open the 276th HODLer Airdrop. A total of 200,000 NAORIS will be distributed. Users only need to hold 1 GT to participate for free, with no lock-up period or deduction of funds. The event ends on 2025 July 31 at 18:00 (UTC+8). All tokens will be released in a single, 100% unlocked distribution. NAORIS spot trading begins that same day at 20:00 (UTC+8), with the initial trading pair NAORIS/USDT.





